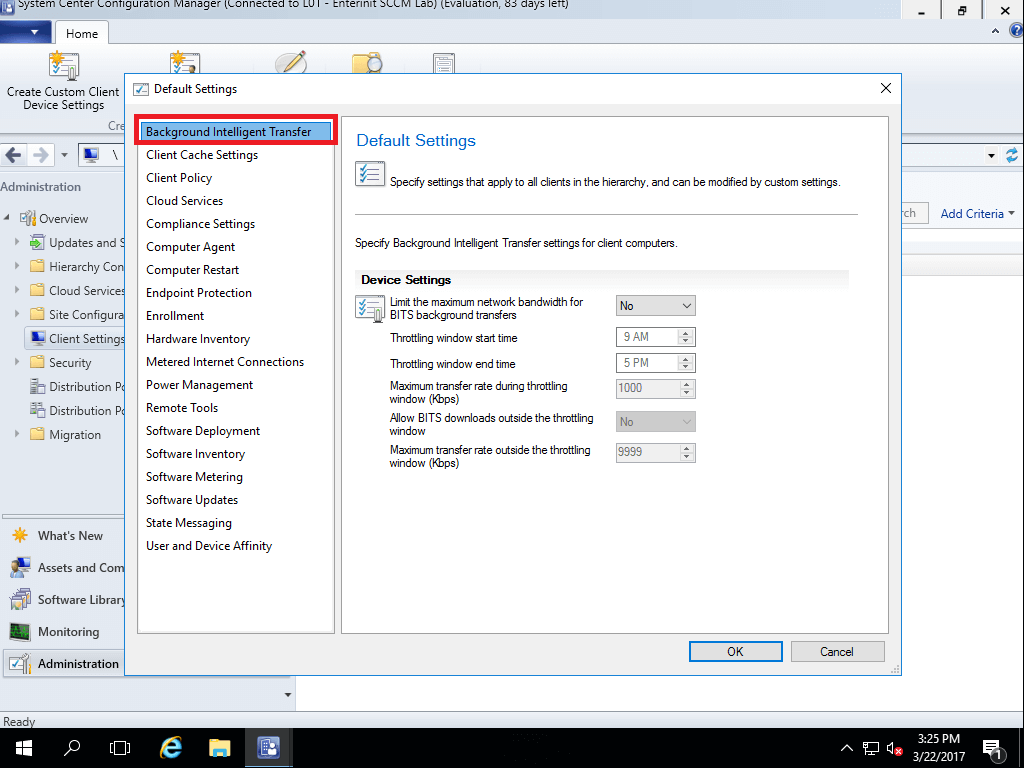
Understanding Configuration Manager 1610 client settings for efficient network usage. Open SCCM Console, navigate to Administration\Client Settings. Selecteer Default Client Settings en klik Eigenschappen in upper menu.
Background Intelligent Transfer Service
- Limit the maximum network bandwidth for BITS background transfers
When this option is True of Yes, the clients will use BITS bandwidth throttling.
- Throttling window start time
Specify the local start time for the BITS throttling window.
- Throttling window end time
Specify the local end time for the BITS throttling window. If equal to Throttling window start time, BITS throttling is always enabled.
- Maximum transfer rate during throttling window (Kbps)
Specify the maximum transfer rate that clients can use during the window.
- Allow BITS downloads outside the throttling window
Choose this option to allow Configuration Manager clients to use separate BITS settings outside the specified window.
- Maximum transfer rate outside the throttling window (Kbps)
Specify the maximum transfer rate that clients will use outside the BITS throttling window when you have chosen to allow BITS throttling outside the window.
Client cache settings
- Configure BranchCache
Beginning in version 1606, use this setting to set up the client computer for BranchCache. To allow BranchCache caching on the client, set Enable BranchCache naar Yes.
- Configure client cache size
The client cache on Windows computers stores temporary files used to install applications and programs. Choose Yes to specify Maximum cache size (megabytes or percentage of disk). If this option is No, the default size is 5,120 MB.
- Configure peer-to-peer
Enable pee-to-peer (HTTP or HTTPS) at client in full OS to share content (clients can get updates not only from Distribution Points and from another PC’s in network). When enabled automatically creates firewalls rules.
Client policy
- Client policy polling interval (minutes)
Specify how frequently the following Configuration Manager clients download client policy:
- Windows computers (Bijvoorbeeld, desktops, servers, laptops)
- Mobile devices that Configuration Manager enrolls
- Mac computers
- Computers that run Linux or UNIX
- Enable user policy polling on clients
When you set this option to True of Yes, and Configuration Manager has discovered the user, clients on computers receive applications and programs that are targeted to the logged-on user.
Because the Application Catalog receives the list of available software for users from the site server, this setting does not have to be True of Yes for users to see and request applications from the Application Catalog. But if this setting is False of No, the following will not work when users use the Application Catalog:
- Users cannot install the applications that they see in the Application Catalog.
- Users will not see notifications about their application approval requests. In plaats van, they must refresh the Application Catalog and check the approval status.
- Users will not receive revisions and updates for applications that are published to the Application Catalog. But they will see changes to application information in the Application Catalog.
- If you remove an application deployment after the client has installed the application from the Application Catalog, clients continue to check that the application is installed for up to 2 dagen.
In addition, when this setting is False of No, users will not receive required applications that you deploy to users or any other management tasks in user policies.
This setting applies to users when their computer is on the intranet and the Internet. It must be True of Yes if you also want to enable user policies on the Internet.
- Enable user policy requests from Internet clients
When the client and site are configured for Internet-based client management and you set this option as True of Yes and both following conditions apply, users receive the user policy when their computer is on the Internet:
- DeEnable user policy polling on client’s client setting is True, of Enable user policy on clients is Yes.
- The Internet-based management point successfully authenticates the user by using Windows authentication (Kerberos or NTLM).
If you leave this option as False of No, or if either of the conditions fails, a computer on the Internet will receive computer policies only. In this scenario, users can still see, request, and install applications from an Internet-based Application Catalog. If this setting is False of No but Enable user policy polling on clients is True of Enable user policy on clients is Yes, users will not receive user policies until the computer is connected to the intranet.
OPMERKING: Application approval requests from users do not require user policies or user authentication.
Cloud Services
- Allow access to cloud distribution point
If you deployed cloud distribution point you can enable or disable access to it for users and devices.
Compliance settings
- Schedule compliance evaluation
Choose Schedule to create the default schedule that will be shown to users when they deploy a configuration baseline. This value can be configured for each baseline in the Deploy Configuration Baseline dialog box.
- Enable User Data and Profiles
Choose Yes if you want to deploy user data and profiles configuration items to Windows 8 or higher computers in your hierarchy.
Computer agent
- Default Application Catalog website point
Configuration Manager uses this setting to connect users to the Application Catalog from Software Center. You can specify a server that hosts the Application Catalog website point by its NetBIOS name or FQDN, specify automatic detection, or specify a URL for customized deployments. In most cases, automatic detection is the best choice because it offers the following benefits:
- Clients are automatically given an Application Catalog website point from their site, if their site has an Application Catalog website point.
- Application Catalog website points on the intranet that are configured for HTTPS are given preference over those that aren’t configured for HTTPS. This helps protect against a rogue server.
- When clients are configured for intranet-based and Internet-based client management, they will be given an Internet-based Application Catalog website point when they are on the Internet and an intranet-based Application Catalog website point when they are on the intranet.
Automatic detection does not guarantee that clients will be given an Application Catalog website point that is closest to them. You might decide not to use Automatically detect for the following reasons:
- You want to manually configure the closest server for clients or ensure that they do not connect to a server across a slow network connection.
- You want to control which clients connect to which server. This might be for testing, performance, or business reasons.
- You do not want to wait up to 25 hours or for a network change for clients to be configured with a different Application Catalog website point.
If you specify the Application Catalog website point rather than use automatic detection, specify the NetBIOS name rather than the intranet FQDN. This helps reduce the likelihood that users will be prompted for credentials when they connect to the Application Catalog on the intranet. To use the NetBIOS name, the following conditions must apply:
- The NetBIOS name is specified in the Application Catalog website point properties.
- You use WINS, or all clients are in the same domain as the Application Catalog website point.
- The Application Catalog website point is configured for HTTP client connections, or it is configured for HTTPS client connections and the web server certificate has the NetBIOS name.
Typically, users are prompted for credentials when the URL has an FQDN but not when the URL is a NetBIOS name. Expect users to be always prompted when they connect from the Internet, because this connection must use the Internet FQDN. When users are prompted for credentials when they are on the Internet, ensure that the server that runs the Application Catalog website point can connect to a domain controller for the user’s account so that the user can be authenticated by using Kerberos.
OPMERKING:
How automatic detection works:
The client makes a service location request to a management point. If there is an Application Catalog website point in the same site as the client, this server is given to the client as the Application Catalog server to use. When more than one Application Catalog website point is available in the site, an HTTPS-enabled server takes precedence over a server that is not enabled for HTTPS. After this filtering, all clients are given one of the servers to use as the Application Catalog; Configuration Manager does not load-balance between multiple servers. When the client’s site does not have an Application Catalog website point, the management point nondeterministically returns an Application Catalog website point from the hierarchy.
When the client is on the intranet, if the chosen Application Catalog website point is configured with a NetBIOS name for the Application Catalog URL, clients are given this NetBIOS name instead of the intranet FQDN. When the client is detected to be on the Internet, only the Internet FQDN is given to the client.
The client makes this service location request every 25 hours or whenever it detects a network change. Bijvoorbeeld, if the client moves from the intranet to the Internet, and the client can locate an Internet-based management point, the Internet-based management point gives Internet-based Application Catalog website point servers to clients.
- Add default Application Catalog website to Internet Explorer trusted sites zone
If this option is True of Yes, the current default Application Catalog website URL is automatically added to the trusted sites zone in Internet Explorer on clients.
This setting ensures that the Internet Explorer setting for Protected Mode is not enabled. If Protected Mode is enabled, the Configuration Manager client might not be able to install applications from the Application Catalog. Standaard, the trusted sites zone also supports user logon for the Application Catalog, which requires Windows authentication.
If you leave this option as False, Configuration Manager clients might not be able to install applications from the Application Catalog unless these Internet Explorer settings are configured in another zone for the Application Catalog URL that clients use.
OPMERKING:
Whenever Configuration Manager adds a default Application Catalog to the trusted sites zone, Configuration Manager removes a previous default Application Catalog URL that Configuration Manager added before it adds a new entry.
Configuration Manager cannot add the URL if it is already specified in one of the security zones. In this scenario, you must either remove the URL from the other zone or manually configure the required Internet Explorer settings.
- Allow Silverlight applications to run in elevated trust mode
This setting must be Yes if users run the Configuration Manager client and use the Application Catalog.
If you change this setting, it takes effect when users next load their browser or refresh their currently opened browser window.
- Organization Name displayed in Software Center
Type the name that users see in Software Center. This branding information helps users to identify this application as a trusted source.
- Use new Software Center
If enabled, all client computers targeted by these client settings will use the new Software Center. Software Center shows user-available apps that were previously accessible only in the Silverlight-dependent Application Catalog.
The Application Catalog website point and Application Catalog web service point site system roles are still required for user-available apps to appear in Software Center.
- Health Attestation
If enabled, SCCM will collect analytics about PC Health (BIOS, BitLocker and other). You can use cloud Attestation Service or On-premise
- Install Permissions
Waarschuwing
This setting applies to the Application Catalog and Software Center. This setting has no effect when users use the company portal.
Configure how users can initiate the installation of software, software updates, and task sequences:
- All Users: Users logged on to a client computer with any permission except Guest can initiate the installation of software, software updates, and task sequences.
- Only Administrators: Users logged on to a client computer must be a member of the local Administrators group to initiate the installation of software, software updates, and task sequences.
- Only Administrators and primary users: Users logged on to a client computer must be a member of the local Administrators group or a primary user of the computer to initiate the installation of software, software updates, and task sequences.
- No Users: No users logged on to a client computer can initiate the installation of software, software updates, and task sequences. Required deployments for the computer are always installed at the deadline. Users cannot initiate the installation of software from the Application Catalog or Software Center.
- Suspend BitLocker PIN entry on restart
If the BitLocker PIN entry is configured on computers, this option can bypass the requirement to enter a PIN when the computer restarts after a software installation.
- Always: Configuration Manager temporarily suspends the BitLocker requirement to enter a PIN on the next computer startup after it has installed software that requires a restart and has initiated a restart of the computer. This setting applies only to computer restarts that are initiated by Configuration Manager and does not suspend the requirement to enter the BitLocker PIN when the user restarts the computer. The BitLocker PIN entry requirement is resumed after Windows startup.
- Never: Configuration Manager does not suspend the BitLocker requirement to enter a PIN on the next computer startup after it has installed software that requires a restart. In this scenario, the software installation cannot finish until the user enters the PIN to finish the standard startup process and load Windows.
- Additional software manages the deployment of applications and software updates
Enable this option only if one of the following conditions apply:
- You use a vendor solution that requires this setting to be enabled.
- You use the Configuration Manager software development kit (SDK) to manage client agent notifications and the installation of applications and software updates.
Waarschuwing
If you choose this option when neither of these conditions applies, software updates and required applications will not be installed on clients. This setting does not prevent users from installing applications from the Application Catalog, or prevent packages, programma's, and task sequences from being installed on client computers.
- PowerShell execution policy
Configure how Configuration Manager clients can run Windows PowerShell scripts. These scripts are often used for detection in configuration items for compliance settings. They can also be sent in a deployment as a standard script.
- Omzeilen: The Configuration Manager client bypasses the Windows PowerShell configuration on the client computer so that unsigned scripts can run.
- Beperkt: The Configuration Manager client uses the current Windows PowerShell configuration on the client computer. This configuration determines whether unsigned scripts can run.
- Allemaal ondertekend: The Configuration Manager client runs scripts only if a trusted publisher has signed them. This restriction applies independently from the current Windows PowerShell configuration on the client computer.
This option requires at least Windows PowerShell version 2.0. The default is Allemaal ondertekend.
Tip
If unsigned scripts fail to run because of this client setting, Configuration Manager reports this error in the following ways:
- Error ID0X87D00327 and the description of Script is not signed as a deployment status error in the Monitoring workspace of the Configuration Manager console.
- Error codes and descriptions of0X87D00327 En Script is not signed of 0X87D00320 En The script host has not been installed yet with the error type of Discovery Error in reports. An example is Details of errors of configuration items in a configuration baseline for an asset.
- The messageScript is not signed (Fout: 87D00327; Source: CCM) in the loggen file.
- Disable deadline randomization
This setting determines whether the client uses an activation delay of up to 2 hours to install required software updates when the deadline is reached. Standaard, the activation delay is disabled.
For virtual desktop infrastructure (VDI) scenarios, this delay can help to distribute the CPU processing and data transfer for a computer that has multiple virtual machines that run the Configuration Manager client. Even if you do not use VDI, if many clients install the same updates at the same time, this can negatively increase CPU usage on the site server. It can also slow down distribution points and significantly reduce the available network bandwidth.
If required software updates must be installed without delay when the configured deadline is reached, choose Yes for this setting.
- Grace period for enforcement after deployment deadline (hours)
In some cases, you might want to give users more time to install required application deployments or software updates beyond any deadlines you configured. This might typically be required when a computer has been turned off for an extended period of time and needs to install a large number of application or update deployments. Bijvoorbeeld, if a user has just returned from vacation, they might have to wait for a long while as overdue application deployments are installed. To help solve this problem, you can define an enforcement grace period by deploying Configuration Manager client settings to a collection.
You can set a grace period of 1 naar 120 hours. This setting is used in conjunction with the deployment property Delay enforcement of this deployment according to user preferences.
Computer restart
When you specify these computer restart settings, ensure that the value for the restart temporary notification interval and the value for the final countdown interval are shorter in duration than the shortest maintenance window that is applied to the computer.
Endpoint Protection
- Manage Endpoint Protection client on client computers
Choose True of Yes if you want to manage existing Endpoint Protection clients on computers in your hierarchy.
Choose this option if you have already installed the Endpoint Protection client and want to manage it with Configuration Manager.
Aanvullend, choose this option if you want to create a script to uninstall an existing antimalware solution, install the Endpoint Protection client, and deploy this script by using a Configuration Manager application or package and program.
- Install Endpoint Protection client on client computers
Choose True of Yes to install and enable the Endpoint Protection client on client computers where it is not already installed.
OPMERKING: If the Endpoint Protection client is already installed, choosing False of No will not uninstall the Endpoint Protection client. To uninstall the Endpoint Protection client, set the Manage Endpoint Protection client on client computers client setting to False of No. Then, deploy a package and program to uninstall the Endpoint Protection client.
- For Windows Embedded devices with write filters, commit Endpoint Protection client installation (requires restart)
Choose Yes to disable the write filter on the Windows Embedded device and restart the device. This commits the installation on the device.
Als No is specified, the client is installed on a temporary overlay that is cleared when the device is restarted. In this scenario, the Endpoint Protection client is not committed until another installation commits changes to the device. This is the default setting.
- Suppress any required computer restarts after the Endpoint Protection client is installed
Choose True of Yes to suppress a computer restart if it is required after the Endpoint Protection client is installed.
Important
If the Endpoint Protection client requires a computer restart and this setting is False, the restart will occur regardless of any maintenance windows that have been configured.
- Allowed period of time users can postpone a required restart to complete the Endpoint Protection installation (hours)
Specify the number of hours that users can postpone a computer restart if this is required after the Endpoint Protection client is installed. This option can be configured only if the Suppress any required computer restarts after the Endpoint Protection client is installed option is False.
- Disable alternate sources (like Windows Update, Microsoft Windows Server Update Services, or UNC shares) for the initial definition update on client computers
Choose True of Yes if you want Configuration Manager to install only the initial definition update on client computers. This setting can be helpful to avoid unnecessary network connections and reduce network bandwidth during the initial installation of the definition update.
Enrollment
- Mobile device enrollment profile
Before you can configure this setting, you must first set to Yes the enrollment user setting Allow users to enroll mobile devices and Mac computers. Then you can choose Set Profile to specify an enrollment profile that has information about the certificate template to use during the enrollment process, the site that has an enrollment point and enrollment proxy point, and the site that will manage the device after the enrollment.
Important
Ensure that you have configured a certificate template to use for mobile device enrollment or for Mac client certificate enrollment before you configure this option.
Mobile devices
- Mobile device enrollment profile
Before you can configure this setting, you must first set to True the mobile device user setting Allow users to enroll mobile devices. Then you can choose Set Profile to specify an enrollment profile that has information about the certificate template to use during the enrollment process, the site that has an enrollment point and enrollment proxy point, and the site that will manage the device after the enrollment.
Important
Ensure that you have configured a certificate template to use for mobile device enrollment before you configure this option.
Hardware inventory
- Maximum custom MIF file size (KB)
Specify the maximum size, in kilobytes, allowed for each custom Management Information Format (MIF) file that will be collected from a client during a hardware inventory cycle. If any MIF files exceed this size, the Configuration Manager hardware inventory will not process them. You can specify a size of 1 naar 5,000 KB. Standaard, this value is set to 250 KB. This setting does not affect the size of the regular hardware inventory data file.
OPMERKING: This setting is available only in the default client settings.
- Hardware inventory classes
In Configuration Manager, you can extend the hardware information that you collect from clients without manually editing the sms_def.mof file. Choose Set Classes if you want to extend Configuration Manager hardware inventory.
- Collect MIF files
Use this setting to specify whether to collect MIF files from Configuration Manager clients during hardware inventory.
For a MIF file to be collected by hardware inventory, it must in the correct location on the client computer. Standaard, the files are located as follows:
- IDMIF files should be in the Windows\System32\CCM\Inventory\Idmif folder.
- NOIDMIF files should be in the Windows\System32\CCM\Inventory\Noidmif folder.
OPMERKING: This setting is available only in the default client settings.
- Maximum random delay
The collection of hardware information is randomized by up to four hours so that the operation doesn’t take place simultaneously on all clients. You can set the maximum delay in order to constrain the time during which the operation takes place.
Metered Internet connections
You can manage how Windows client computers communicate with Configuration Manager sites when they use metered Internet connections. Internet providers sometimes charge by the amount of data that you send and receive when you are on a metered Internet connection.
OPMERKING: The configured client setting is not applied to Windows 8 client computers in the following scenarios:
- The computer is on a roaming data connection: The Configuration Manager client does not perform any tasks that require data to be transferred to Configuration Manager sites.
- The Windows network connection properties are configured as non-metered: The Configuration Manager client behaves as if this is a non-metered Internet connection and so transfers data to the Configuration Manager sites.
- Client communication on metered Internet connections
From the drop-down list, choose one of the following for Windows client computers:
- Allow: All client communications are allowed over the metered Internet connection unless the client device is using a roaming data connection.
- Limit: Only the following client communications are allowed over the metered Internet connection:
- Client policy retrieval
- Client state messages to send to the site
- Software installation requests by using the Application Catalog
- Required deployments (when the installation deadline is reached)
Important
If a user initiates a software installation from Software Center or the Application Catalog, these are always permitted, regardless of the metered Internet connection settings.
If the data transfer limit is reached for the metered Internet connection, the client no longer tries to communicate with Configuration Manager sites.
- Block: The Configuration Manager client does not try to communicate with Configuration Manager sites when it is on a metered Internet connection. This is the default value.
Power management
- Allow users to exclude their device from power management
From the drop-down list, choose True of Yes to let users of Software Center exclude their computer from any configured power management settings.
- Enable wake-up proxy
Specificeer Yes to supplement the site’s Wake On LAN setting when it is configured for unicast packets.
Waarschuwing
Do not enable wake-up proxy in a production network without first understanding how it works and evaluating it in a test environment.
- Wake-up proxy port number (UDP)
Keep the default value for the port number that managed computers use to send wake-up packets to sleeping computers. Or, change the number to a value of your choice.
The port number specified here is automatically configured for clients that run Windows Firewall when you use the Windows Firewall exception for wake-up proxy optie. If clients run a different firewall, you must manually configure it to allow the UDP port number that is specified for this setting.
- Wake On LAN port number (UDP)
Keep the default value of 9, unless you have changed the Wake On LAN (UDP) port number on the Ports tab of the site Eigenschappen.
Important
This number must match the number in the site Properties. If you change this number in one place, it isn’t automatically updated in the other place.
Remote tools
- Enable Remote Control on clients En Firewall exception profiles
Choose whether Configuration Manager remote control is enabled for all client computers that receive these client settings. Choose Configureer to enable remote control. Optionally, configure firewall settings to allow remote control to work on client computers.
Remote control is disabled by default.
Important
If firewall settings are not configured, remote control might not work correctly.
- Users can change policy or notification settings in Software Center
Choose whether users can change remote control options from within Software Center.
- Allow Remote Control of an unattended computer
Choose whether an admin can use remote control to access a client computer that is logged off or locked. Only a logged-on and unlocked computer can be remotely controlled when this setting is disabled.
- Prompt user for Remote Control permission
Choose whether the client computer will show a message that asks for the user’s permission before allowing a remote control session.
- Grant Remote Control permission to local Administrators group
Choose whether local admins on the server that initiates the remote control connection can establish remote control sessions to client computers.
- Access level allowed
Specify the level of remote control access that will be allowed. You can choose from:
- Volledige controle
- View only
- None
- Permitted viewers
Choose Set Viewers to open the Configure Client Setting dialog box and specify the names of the Windows users who can establish remote control sessions to client computers.
- Show session notification icon on taskbar
Choose this option to show an icon on the taskbar of client computers to indicate that a remote control session is active.
- Show session connection bar
Choose this option to show a high-visibility session connection bar on client computers to indicate that a remote control session is active.
- Play a sound on client
Choose this option to use sound to indicate when a remote control session is active on a client computer. You can play a sound when the session connects or disconnects, or you can play a sound repeatedly during the session.
- Manage unsolicited Remote Assistance settings
Choose this option to let Configuration Manager manage unsolicited remote assistance sessions.
In an unsolicited remote assistance session, the user at the client computer did not request assistance to initiate the session.
- Manage solicited Remote Assistance settings
Choose this option to let Configuration Manager manage solicited remote assistance sessions.
In a solicited remote assistance session, the user at the client computer sent a request to the admin for remote assistance.
- Level of access for Remote Assistance
Choose the level of access to assign to remote assistance sessions that are initiated in the Configuration Manager console.
OPMERKING: The user at the client computer must always grant permission for a Remote Assistance session to occur.
- Manage Remote Desktop settings
Choose this option to let Configuration Manager manage Remote Desktop sessions for computers.
- Allow permitted viewers to connect by using Remote Desktop connection
Choose this option to let users specified in the permitted viewer list to be added to the Remote Desktop local user group on client computers.
- Require network level authentication on computers that run Windows Vista operating system and later versions
Choose this more secure option if you want to use network-level authentication to establish Remote Desktop connections to client computers that run Windows Vista or later. Network-level authentication requires fewer remote computer resources initially because it finishes user authentication before it establishes a Remote Desktop connection. This method is more secure because it can help protect the computer from malicious users or software, and it reduces the risk from denial-of-service attacks.
Software deployment
- Schedule re-evaluation for deployments
Configure a schedule for when Configuration Manager re-evaluates the requirement rules for all deployments. The default value is every 7 dagen.
Important
We recommend that you do not change this value to a lower value than the default. Doing that might negatively affect the performance of your network and client computers.
You can also initiate this action from a Configuration Manager client computer by choosing the action Application Deployment Evaluation Cycle from the Actions tab of Configuratiemanager in Control Panel.
Software inventory
- Inventory reporting detail
Specify the level of file information to inventory. You can inventory details about the file, details about the product associated with the file, or all information about the file.
- Inventory these file types
If you want to specify the types of file to inventory, choose Set Types and then configure the following in the Configure Client Setting dialog box:
OPMERKING: If multiple custom client settings are applied to a computer, the inventory that each setting returns will be merged.
- Choose theNieuw icon to add a new file type to inventory. Then, specify the following information in the Inventoried File Properties dialog box:
- Naam: Provide a name for the file that you want to inventory. You can use the\ character to represent any string of text and the ? character to represent any single character. Bijvoorbeeld, if you want to inventory all files with the extension .doc, specify the file name *.doc.
- Location: ChooseSet to open the Path Properties dialog box. You can configure software inventory to search all client hard disks for the specified file, search a specified path (Bijvoorbeeld, C:\Folder), or search for a specified variable (Bijvoorbeeld, %windir%). You can also search all subfolders under the specified path.
- Exclude encrypted and compressed files: When you choose this option, any files that have been compressed or encrypted will not be inventoried.
- Exclude files in the Windows folder: When you choose this option, any files in the Windows folder and its subfolders will not be inventoried.
- ChooseOK to close the Inventoried File Properties dialog box.
- Add all the files that you want to inventory, and then chooseOK to close the Configure Client Setting dialog box.
- Collect files
If you want to collect files from client computers, choose Set Files and then configure the following:
OPMERKING: If multiple custom client settings are applied to a computer, the inventory that each setting returns will be merged.
- In de Configure Client Setting dialog box, choose the Nieuw icon to add a file to be collected.
- In deCollected File Properties dialog box, provide the following information:
- Naam: Provide a name for the file that you want to collect. You can use the\ character to represent any string of text and the ? character to represent any single character.
- Location: ChooseSet to open the Path Properties dialog box. You can configure software inventory to search all client hard disks for the file that you want to collect, search a specified path (Bijvoorbeeld, C:\Folder), or search for a specified variable (Bijvoorbeeld, %windir%). You can also search all subfolders under the specified path.
- Exclude encrypted and compressed files: When you choose this option, any files that have been compressed or encrypted will not be collected.
- Stop file collection when the total size of the files exceeds (KB): Specify the file size (in kilobytes) after which no more of the files specified underNaam will be collected.
OPMERKING:
- The site server collects the five most recently changed versions of collected files and stores them in the<ConfigMgr installation directory>\Inboxes\Sinv.box\Filecol directory. If a file has not changed since the last software inventory was collected, the file will not be collected again.
- Software inventory does not collect files larger than 20 MB.
- The valueMaximum size for all collected files (KB) in the Configure Client Setting dialog box shows the maximum size for all collected files. When this size is reached, file collection will stop. Any files already collected are retained and sent to the site server.
Important
- If you configure software inventory to collect many large files, this might negatively affect the performance of your network and site server.
- ChooseOK to close the Collected File Properties dialog box.
- Add all the files that you want to collect, and then chooseOK to close the Configure Client Setting dialog box.
- Set Names
During software inventory, manufacturer names and product names are retrieved from the header information of files installed on clients in the site. Because these names are not always standardized in the file header information, when you view software inventory information in Resource Explorer or run queries, different versions of the same manufacturer or product name can sometimes appear. If you want to standardize these display names, choose Set Names and then configure the following in the Configure Client Setting dialog box:
- Name type: Software inventory collects information about both manufacturers and products. From the drop-down list, choose whether you want to configure display names for a Manufacturer or a Product.
- Display name: Specify the display name that you want to use in place of the names in theInventoried names You can choose the Nieuw icon to specify a new display name.
- Inventoried names: Choose theNieuw icon to add a new inventoried name that will be replaced in software inventory by the name chosen in the Display name You can add multiple names that will be replaced.
Software Metering
- Device Settings
After you collect usage data from Configuration Manager clients, you can view the data in different ways, which includes using collections, queries, and reporting. This data, combined with data from software inventory, can help your organization to determine the following:
- How many copies of a particular software program have been deployed to the computers in your organization. Among those computers, you can determine how many users actually run the program.
- How many licenses of a particular software program you have to purchase when you renew your license agreement with the software vendor.
- Whether users are still running a particular software program. If the program is not being used, you might retire the program.
- Which times of the day a software program is most frequently used.
Software updates
- Enable software updates on clients
Use this setting to enable software updates on Configuration Manager clients. When you disable this setting, Configuration Manager removes existing deployment policies from client. When you re-enable this setting, the client downloads the current deployment policy.
Important
When you disable this setting, NAP and compliance settings policies that rely on the device setting for software updates will no longer function.
- Software update scan schedule
Use this setting to specify how often the client initiates a software update compliance assessment scan. The compliance assessment scan determines the state for software updates on the client (Bijvoorbeeld, required or installed).
Standaard, a simple schedule is used and the compliance scan is initiated every 7 dagen. You can choose to create a custom schedule to specify an exact start day and time, choose whether to use UTC or the local time, and configure the recurring interval for a specific day of the week.
OPMERKING: If you specify an interval of less than 1 dag, Configuration Manager will automatically default to 1 dag.
Waarschuwing
The actual start time on client computers is the start time plus a random amount of time up to 2 hours. This prevents client computers from initiating the scan and connecting to Windows Server Update Services (WSU's) on the active software update point server at the same time.
- Schedule deployment re-evaluation
Use this setting to configure how often the Software Updates Client Agent re-evaluates software updates for installation status on Configuration Manager client computers. When software updates that were previously installed are no longer found on client computers and are still required, they are reinstalled.
The deployment re-evaluation schedule should be adjusted based on company policy for software update compliance, whether users have the ability to uninstall software updates, and so on. Remember that every deployment re-evaluation cycle results in some network and client computer CPU activity. Standaard, a simple schedule is used and the deployment re-evaluation scan is initiated every 7 dagen.
OPMERKING: If you specify an interval of less than 1 dag, Configuration Manager will automatically default to 1 dag.
- When any software update deadline is reached, install all other software update deployments with deadline coming within a specified period of time
Use this setting to install all software updates in required deployments that have deadlines that will occur within a specified period of time. When a deadline is reached for a required software update deployment, installation is initiated on clients for the software updates in the deployment. This setting determines whether to also initiate the installation for software updates defined in other required deployments that have a configured deadline within the specified period of time.
Use this setting to expedite software update installation for required software updates, potentially increase security, potentially decrease display notifications, and potentially decrease system restarts on client computers. Standaard, this setting is not enabled.
- Period of time for which all pending deployments with deadline in this time will also be installed
Use this setting to specify the timeframe for the previous setting. You can enter a value from 1 naar 23 hours and from 1 naar 365 dagen. Standaard, this setting is configured for 7 dagen.
- Enable installation of Express installation files on clients
When you use a supported version of Windows 10, you can now use Configuration Manager settings to download only the delta between the current month’s Windows 10 Cumulative Update and the previous month’s update. Currently in Configuration Manager Current Branch, the full Windows 10 Cumulative Update (including all updates from previous months) are downloaded each month. Using express installation files provides for smaller downloads and faster installation times on clients.
Important
While the settings to support the use of express installation files is available in Configuration Manager, this functionality is only supported in Windows 10 versie 1607 with a Windows Update Agent update included with the updates released on January 10, 2017 (Patch Tuesday). You can take advantage of express installation files when the next set of updates are released on February 14, 2017. Ramen 10 versie 1607 without the update and prior versions do not support express installation files.
State Messaging
- State message reporting cycle (minutes)
You can config, how frequently SCCM check clients state.
User and device affinity

- User device affinity usage threshold (minutes)
Specify the number of minutes before Configuration Manager creates a user device affinity mapping.
- User device affinity usage threshold (dagen)
Specify the number of days over which the usage-based affinity threshold is measured.
OPMERKING: Bijvoorbeeld, als User device affinity usage threshold (minutes) is specified as 60 minutes and User device affinity usage threshold (dagen) is specified as 5 dagen, the user must use the device for 60 minutes over a period of 5 days to automatically create a user device affinity.
- Automatically configure user device affinity from usage data
Choose True of Yes to let Configuration Manager automatically create user device affinities based on the usage information that is collected.
- Allow user to define their primary devices
Specify whether users are allowed to identify their own primary devices on the My Devices tab of the Application Catalog.